
While the stereotypical hacker we see in Hollywood movies frantically types away at his keyboard from his parent’s basement, trying random passwords to gain access to his high school grading system or a local bank – the reality is far from this. The modern hacking criminal is a con-man, well-spoken and knows how to gain your trust using a number of techniques.
“Electronic” hacking is difficult- simply asking for a password is easier
Security systems that look for patterns attributed to attacks are becoming cheaper, passwords longer and more complicated and security departments are growing year on year.
But why go to so much trouble when you can just ask someone for their password? It may sound simple, but this is what is happening. Humans by nature are flawed and when presented with a situation that puts us out of our “comfort zone” we tend to become stressed and make poor decisions. While a company may have a water-tight security policy in place, having staff comply with the policy 100% of the time is a challenge far beyond the initial undertaking of creating the rules.
Social engineering
Social engineering deals with a number of techniques that are used to gain access to a system by the path of least resistance – your staff and customers. These techniques range from impersonating an angry customer who has lost his password and needs a new one because he has an emergency to asking for someone to “hold open the door” when entering a secure facility. Often, surveillance is used to gather information that can range from in-person spying to simply “Googling” the victim or viewing their social media feeds.
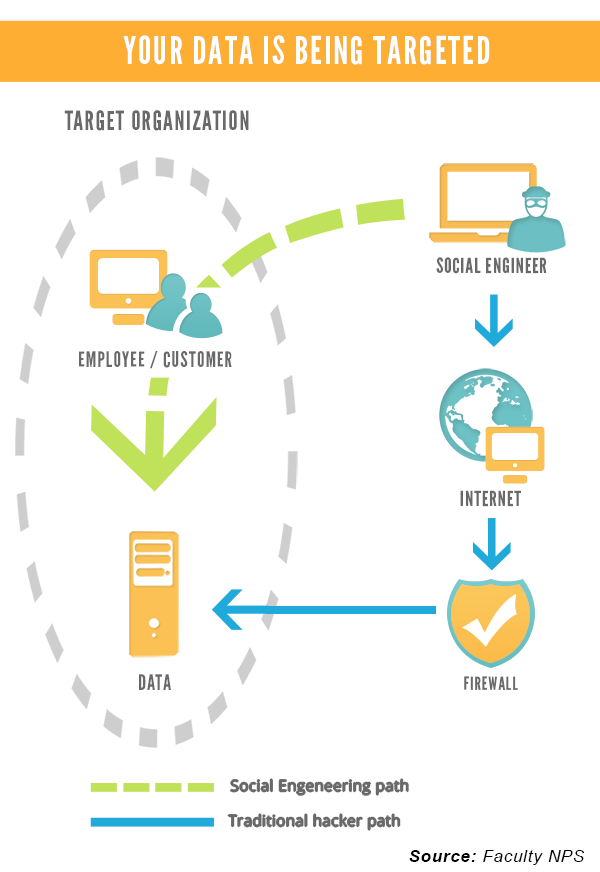
How to combat these security threats:
1. Educate staff and customers on potential red flags, for example; emails or phone calls asking for passwords. It is, of course, important to also follow these rules and never ask for passwords.
2. Create a comprehensive security policy that covers definitions, best practices, procedures and emergency plans in case of a breach. Most security incidents are visible and become worse because they are not addressed immediately. These policies should also be tested regularly with real world situations and plans for retraining.
3. Open up channels for reporting suspicious events. This applies to internal staff and customers. In so many cases there are instances where email addresses used for reporting abuse or security issues are not monitored nor responded to. It is important to create a culture where it is “okay” to report things that are out of the ordinary.
4. Never bypass policies and procedures. We are often tempted to take a shortcut when under stress, but cool heads prevail when it comes to security.
Above all, as part of a paperless strategy it is important to be aware of all possible threats.
Phishing, for instance, cannot be stopped entirely, but there are methods to combat it both technically and through education, for example:
- Sign messages using DKIM
- Personalize emails (with multiple pieces of data and partial data)
- Implement, monitor and refine DMARC rules and policies
- Never request personal sensitive information from customers by email or phone
- Attach shared-secret protected documents instead of linking to a portal
If you are concerned about your digital security, don’t hesitate any longer – rather chat to an expert before it’s too late…
Improve the customer experience with secure document delivery today














