
“How to safely use email to communicate with your banking clients, while reducing phishing attacks by 98.5%.”
This newsletter is designed to be a quick reference for bank personnel who are responsible for combating phishing. We tackle head-on the thorny problems about phishing that have been very difficult to solve. This guide presents a holistic approach to addressing phishing that makes most of those problems effectively go away.
We cannot stop phishing. However, we can raise the bar sufficiently to make phishing no longer economically worthwhile.
Phishing and Identity Theft: What Fraudsters Know That You Don’t
Today, businesses are struggling with online security challenges because they are ignoring key principles and trying to replace them with new and often unproven techniques.
In recent years many banks have adopted the technique of vetoing email as a valid client communication tool. However, we live in an age where email has grown to become the most common form of business communication.
Email has surpassed the fax and postal mail, and is now relied upon for critical communication thanks to its ease of use, speed and low cost. Email is used for everything from financial instructions, to sending contracts and legal documents, to sharing confidential information like patient records, patent applications and business plans. Email is used for almost any type of communication imaginable, but banned by certain banks.
This makes no sense to the consumer. Every other service provider is communicating with them via email, and so consumers expect the bank to do so too. When an email arrives purporting to come from the bank, they eagerly open, read and follow the instructions, because they expect email from their bank.
This presents a fundamental problem of principle. Clients expect email from their bank. Even though the bank informs their clients that they will NOT send email, the client does not grasp that there is a potential risk when they DO receive an email purporting to come from the bank.
Phishing scams are predicated on this principle. Phishers’ use of email as a communication tool is assisted by the fact that the banks have chosen not to use the VERY same channel that phishers use for comparative education. As a result, the client is left totally defenceless in identifying a phishing email.
The paradigm shift thinking is that the bank should not STOP sending email, but should send MORE email in a structured, defined and identifiable manner.
By communicating more frequently by email, the consumer can be educated about how to identify a phishing email, thus significantly reducing successful phishing attacks. This is confirmed by David Bell, chief executive of the Australian Bankers’ Association, who says,
“Banks tell us that customers are reporting fewer incidents of online fraud due to the industry’s efforts in fraud prevention such as employee training, strict privacy policies and… communicating with customers and educating them on how to avoid becoming a phishing victim. These combined efforts have resulted in a comparatively low level of fraud in Australia compared to the UK and other countries.”
Will Phishing Go Away?
The boom in online financial transactions has made phishing a lucrative method of attack for scammers. The risk-to-reward ratio for phishing attacks is exceptionally favorable for the attacker. The cost and ease of sending emails and setting up a web presence are trivial. As with spam, the fact that so many millions of people can be targeted makes it worthwhile, even with low hit rates. Even if less than 0.1 percent of the targeted victims respond, phishing emails can be extraordinarily productive. In addition, prosecuting the perpetrators of phishing attacks has proven to be nigh on impossible.
Can We Win the War?
A prominent anti-phishing technique is to employ net monitoring services to find and shut down phishing websites and URL’s. This is a key feature in the current phishing defense strategy. Banks cannot stop the email attacks from reaching their customers, and so they attempt to prevent the websites from collecting the information. Unfortunately this technique is only effective after the fact, typically after being notified of an attack by a customer or monitoring service. Phishers are still able to profit by acting swiftly once they have launched the attack.
“Pharms” Springing Up
The real issue with this technique is that phishers are now creating unique, distributed “pharms” of websites to collect the information – making it impossible to shut down all the data collection points.
How Significant is the Problem?
According to Netcraft, there were more than 609,000 confirmed phishing URLs in 2006, an enormous jump from just 41,000 in 2005. But there is an alarming sting in this tail – almost half the total came in a single month, December. A staggering 277,000 unique URLs were detected in December 2006 alone, with 457,000 cumulatively in the last three months of the year.
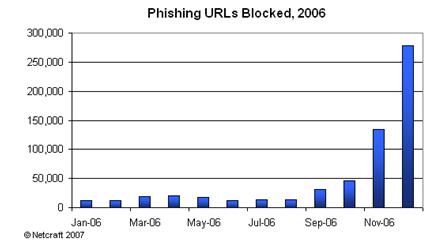
Netcraft’s explanation for the sudden surge is the emergence of phishing-creation kits known collectively as “Rockfish” (or “R11”), which automate the rapid creation of scam websites. These allow sophisticated domain management, including webs of sub-domains, as part of the battle to overwhelm anti-phishing systems with vast numbers of short-lived sites that are impossible to keep tabs on or block.
This trend can only increase
If the Netcraft statistics are anything to go by, this trend is likely to continue its acceleration in 2007, meaning that anti-phishing engineers are now facing the prospect of having to block swarms of anti-phishing sites in real time to make any impression on the phenomenon.
Another interesting indicator is the rise in the number of companies being targeted by criminals, which reached a total of 942 during the year. The range was also noteworthy, with many companies beyond the usual banking sector now under attack, including online payment gateways, e-commerce retailers, social networking sites, government websites, ISPs, and online gaming portals.
The evidence indicates that phishing shows no signs of abating.
What Technology Can Prevent Phishing?
A November 2006 study of the latest technique – anti-phishing toolbars – has come to a stark conclusion about their effectiveness – none of them are any good.
Finding Phish: An Evaluation of Anti-Phishing Toolbars, was conducted by researchers at Carnegie Mellon University in Pittsburgh, backed by the US National Science Foundation and the US Army Research Office.
The study looked at ten browser toolbars: Microsoft Explorer 7, eBay, Google, Netcraft (Mozilla), Netscape, Cloudmark (Mozilla), Earthlink, Geotrust’s TrustWatch, and Stanford University’s Spoofguard, and McAfee’s SiteAdvisor.
“Overall, we found that the anti-phishing toolbars that were examined in this study left a lot to be desired,” the authors concluded. “Many of the toolbars we tested were vulnerable to some simple exploits as well.”
In an April 2006 study called Why Phishing Works by the Centre for Research in Computation and Society at Harvard University, the authors concluded, “standard security indicators are not effective for a substantial fraction of users”.
The implication? Visual clues on a valid website are too easily replicated by fraudsters, making it nigh on impossible for all but the most astute surfers to differentiate between legitimate and fraudulent sites.
If Phishing Can Never Be Stopped, What Else Can Be Done?
It seems that phishing attacks can never be prevented using traditional techniques. Albert Einstein said: “The significant problems we have cannot be solved at the same level of thinking with which we created them.” Very simply, we need new ideas.
A New Way to Combat Phishing
Banks are undoubtedly the industry most affected by phishing. And with 133 million users of its online payment service worldwide, PayPal (owned by eBay) is one of the most frequent targets of phishing attacks as well.
Says Michael Barrett, Chief Information Security Officer at eBay, “What we’re doing is taking a broad-brush strategy”, when asked what eBay’s phishing strategy is.
And what exactly might that broad-brush strategy be?
- Consumer education;
- Digitally signing all outbound e-mail, and;
- Working with ISP’s to delete email claiming to come from eBay and PayPal, but which doesn’t have the correct digital signature.
“We’re 100% ready to start signing all outbound e-mail [from eBay and PayPal] using both SPF and DomainKeys.”
Now that’s a different level of thinking to conventional wisdom, which says, “We won’t communicate with our banking clients by email because of phishing.”
We applaud eBay for taking comprehensive measures against an acute challenge, and we look forward to reading reports that their phishing attacks have decreased by 98.5% or more, once their testing phase is complete.
So, How Can a Concerned Bank Reduce Phishing?
We do not believe that it is ever possible to reduce the number of phishing attacks, nor the number of people targeted.
What we do believe is that we can ‘raise the bar’ to the cost and effectiveness of phishing attacks by utilizing the principle of “Sender Verification”, coupled with user education, ISP collaboration and finally, anti-fraud technology.
Sender Verification Strategy
The aim of “Sender Verification” is to raise the trust in legitimate email from verified senders. There are many techniques to accomplish this, certain of which are used to some level of success today. However, when used in unison, these individual techniques combine to form a powerful strategy, which has a dramatic effect on quashing phishing attacks.
We recommend a combination of the following:
- S/MIME Digital Signatures
- DKIM (DomainKeys Identified Mail)
- SPF (Sender Policy Framework)
- Striata Anti-Phishing Device
- Personal Challenge Phrase and/or Image
- Web trackback to verify content
Implementing a logical, structured Sender Verification Strategy as described will dramatically curtail the number of phishing emails reaching consumers.
However, human nature and the lucrative rewards of phishing mean that there will still remain a risk, the efficacy of the Sender Verification Strategy notwithstanding.
Conclusion
One has to grudgingly admire the tenacity, creativity and gumption of the phishing world. For them the stakes are high, and the potential rewards means their attacks will not diminish.
Rather than ignoring the problem, there exist proven, readily available solutions which have been highlighted in this article. If the principle of combined techniques is adopted and if each of the techniques results in a 50% reduction of successful phishing attacks, then we will have a 98.5% success rate.



