
In the second part of this series, I will be focusing on the importance of effective password protection when dealing with encrypted, offline documents. As with all encryption, it is important to consider the length and complexity of the password or phrase that is used to generate the key. A short, simple secret becomes the weak link in the chain to an effective secure communication. Attackers can simply brute force attack the document.
Brute force – what it entails and how to combat it
To understand how brute force works, consider a real world example: your ATM card. Most banks require a PIN code consisting of 4 digits (0-9) and allow numbers to be repeated. This simply allows only 9,999 combinations which is secure enough for an ATM (which only allows 3 attempts) because a thief, on average would have to traverse through at least half (4,999) of the possible numbers before guessing correctly.
But what if only 3 numbers were allowed? This significantly reduces the number of possible PIN codes by a factor of 10. Only 2 numbers? Suddenly it becomes possible to guess within a few minutes (if unlimited tries are allowed).
Replace the thief with a computer…
When this concept is translated into a virtual world and a computer (or multiple distributed computers) is guessing the combinations, the strength of the password becomes significantly more important.
As a test, I ran a benchmark of how many passwords my laptop can guess per second. The results: For a 128bit password to open a secure PDF, just fewer than 30,000 different combinations could be tested per second. So, it’s obvious that a 4 digit PIN code is not sufficient if the data contained in the PDF is highly confidential as my PC can run through every 4 digits numeric combination in less than a second.
However it gets a little more complicated as there are 2 factors that influence password strength:
- Length – 2, 3 or 4 “slots”
- Data Set
- Numbers only = 10 possibilities per slot above
- Alphanumeric = 36 possibilities per slot above
- Upper & lowercase = 62 possibilities
- Special characters = Conservatively 67 possibilities per slot above
Combinations of multiple pieces of data, preferably including more than one data set, i.e. both numbers and characters are recommended. This table shows the number of combinations by the length of the password and the type of data being used.
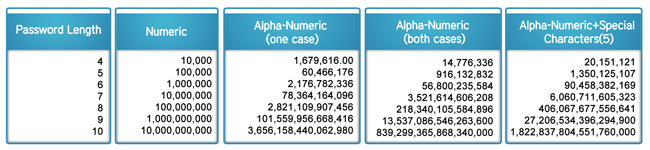
It’s clear that complex passwords should be used to protect confidential documents to ensure a high level of security. But let’s consider that in conjunction with ease of use. Nobody wants to remember a password like <1h4Tep4sSw0rDs!>
The middle ground:
- Fit for purpose – Different document types require different levels of protection. For example, your utility bill does not contain as much sensitive information as your detailed telephone statement.
- Shared secrets – Data that is known to you – like your last name combined with the last four digits of your social security number provides a password mostly greater than 8 characters but still easy to remember.
In must also be noted that even when someone gains access to a document and manages to successfully brute force the password, the algorithm itself has not been broken. They will still only have access to a single document – won’t be able to decode any more documents encrypted with different passwords.
Key points to remember:
- Simple passwords can be found by brute force methods
- Complex passwords provide a higher level of security
- Multiple pieces of data that create alpha and numeric characters create complex passwords, but are still easy to remember
- The password strength should match the level of security needed, there is a way to balance security and ease of use for the customer
If you would like to chat to an email specialist, please get in touch.
Improve the customer experience with secure document delivery today














