
If cyber attacks seem to be escalating, it’s because they are. Every day seems to bring news of yet another major data breach, and increasingly it’s happening to to big companies that you would expect to have watertight information security.
Cyber criminals are malicious, sophisticated, organized and innovative. While organizations are still using single-focus solutions to combat specific attacks, attackers are striking across multiple layers, using their initial compromise to establish a beachhead, from which they can launch subsequent attacks.
Organizations that have strong security in certain areas, could have vulnerabilities in others. If we relate this to a physical security example, it would be like failing to lock your front door because you have a fence.

Organizations need multiple layers of defense
It takes many technologies and processes to provide comprehensive risk and security management.
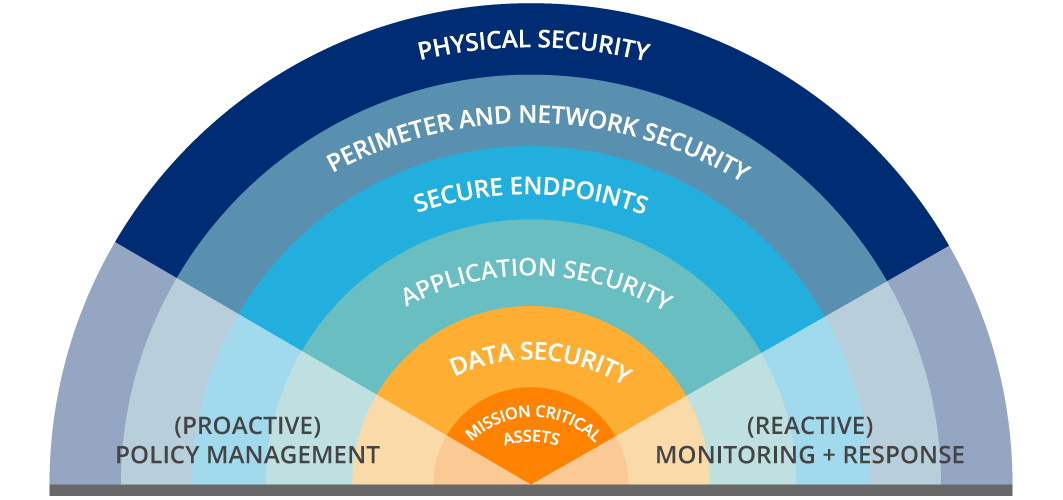
Layered security, or ‘defense in depth’, is a concept of effective security posture, employing multiple tools and different techniques to slow down or stop an attacker.
Some of these layers include the following
- Physical Security – Hacking into network systems is not the only way that sensitive information can be stolen or used against an organization. Physical security must be implemented correctly to prevent attackers from gaining physical access and then accessing what they want from within the trusted network.
- Perimeter and Network Security – The perimeter is so much more complex than it used to be and is no longer as simple as having a firewall. Other systems and processes, such as Intrusion detection system (IDS), Intrusion prevention systems (IPS), Data Loss Prevention (DLP) and segregation also play a major role.
- Secure Endpoints – Each device with a remote connection to the network, creates a potential entry point for security threats. Laptops, USB drives, tablets and smartphones all have the ability to store and access sensitive data. Methods such as patching, antivirus and Multi Factor Authentication all play a role in ensuring that a device doesn’t become an entry point.
- Application Security – Make sure you are developing applications that are designed to be secure and follow the OWASP controls when using 3rd party services or software, be sure to vet their security thoroughly before integrating into your systems.
- Data Security – Depending on what you need to do with your sensitive data, you have a choice of tools available to secure data (e.g. Hashing or encryption), but never let it be stored on a system unprotected.

Back to the physical security example mentioned above …
If an intruder gets through a hole in the fence, they have to make it past the attack dogs, then the security door, then the locked door, get past the security sensors and CCTV cameras undetected,only to find treasure hidden under the bed.
You need to make sure all security layers work well together by implementing these underlying principles
- Actionable plan – A sound security plan is the first step towards a multi-layered defense system
- Policies and procedures – Comprehensive policies and procedures are the groundwork on which all actions should be based.
- Education and awareness – Security-aware employees can be one of the most effective deterrents to malicious threats, but also the weakest link if they don’t follow procedure.
- Monitoring / Detection – Although you may have prevention measures in place, monitoring and detection are essential. Continuously monitor all systems, analyze logs and look for unusual activity.
- Continuous maintenance – The job is never done. The security environment is changing rapidly. What was secure yesterday could be vulnerable today. Continuously check systems for vulnerabilities, learn about new threats, as well as patch and adjust defenses as needed.
- Incident management – Establish good incident response and disaster recovery plans. You don’t want to be developing your plans during a crisis. The management of an incident often has more impact on business’ reputation than the incident itself.
- Remediation – Fix everything, big or small, as soon as possible. What may seem insignificant in isolation, could form an essential part of the security arsenal. Every element represents another layer to break through.
Unfortunately, even with the most amazing security in place, it just takes one person to undo it all. That’s why building a strong security culture is so important.

On the physical security example mentioned above again …
One of the easiest ways to circumvent security is for the criminal to be friends with the homeowner. You’ve invited the intruder into your house and bypassed all the system security for them and maybe even given them a cup of tea to welcome them.
The target can be everybody and everything!
Attackers throw a wide net, hoping for any takers.
Organizations and people need to be prepared on all fronts.
Did you enjoy the read? Then be sure to subscribe to our blog to receive more great posts from our expert bloggers.















