In this final post of my authentication blog series I focus on DMARC and how it uses SPF and DKIM to close the loop on email authentication.
What is Domain-based Message Authentication, Reporting and Conformance (DMARC)?
DMARC basically standardizes how email receivers perform email authentication using SPF and DKIM, enabling consistent results for the sender’s messages.
Most of the major webmail providers: AOL, Gmail, Hotmail, Yahoo would use this authentication reporting tool.
High-level principles of DMARC:
- Senders opt-in by publishing a DMARC policy
- Receivers provide feedback so that Senders can close gaps (and identify phishing attempts)
- Senders increase the level of authenticated email being delivered
- Receivers can identify and block unauthenticated email (as published by the Sender’s DMARC policy)
How DMARC works:
A DMARC policy allows a sender to indicate that their emails are protected by SPF and/or DKIM, and tells a receiver what to do if one or both authentication methods fail. The policy will direct the receiver to mark non-compliant emails as spam, proceed to quarantine or reject the email.
DMARC removes guesswork from the receiver’s handling of these failed messages, limiting or eliminating the end user’s exposure to potentially fraudulent or harmful messages.
DMARC also provides a way for the email Receiver to report back to the sender about emails that pass or fail DMARC evaluation.
A real world example:
Joe works at My Company. My Company has a very security conscious domain administrator who has previously implemented SPF and DKIM on all of the company’s mailservers. He now decides to implement DMARC.
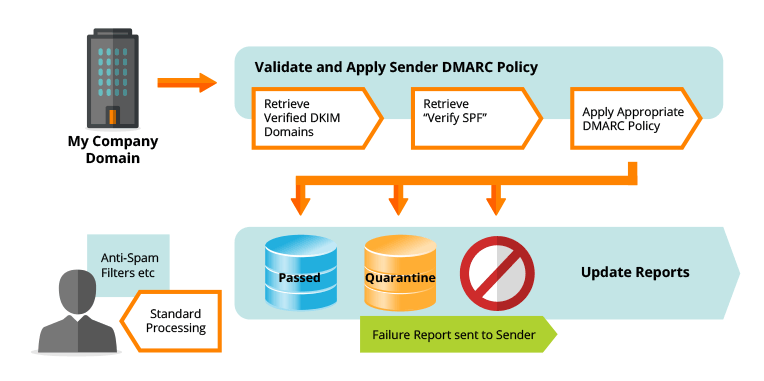
1. My Company’s domain administrator gets his list of domains that send on behalf of the company (Including external vendors/marketers). This list contains the IP addresses of all servers that send emails on MyCompany’s behalf.
2. The domain administrator sets up an email address that will receive all of My Company’s reports regarding DMARC activity.
3. The domain administrator deploys a DMARC DNS record for every domain on his list. When he sets up the configuration, he will specify the following:
a. What email address the reports need to be sent to
b. The policy directive on how to handle emails that fail SPF or DKIM or both, i.e.
i. None – this will deliver to the end user and report back to the domain owner only
ii. Quarantine/Spam – this will deliver to the end users spam folder
iii. Reject – Cancels the email and does not deliver to end user
c. The percentage of messages affected. This is used when the domain owner has not set up policies on all domains, as he is ramping up the deployment of DMARC i.e. he expects only 70% of emails from the organization to pass these tests. This means that only when more than 30% of messages fail, will the DMARC policy be applied. Ultimately, the domain owner should aim at having this policy applied to 100% of emails.
Joe decides to send an email to Mike. He is using a My Company Mailserver that has DMARC set up;
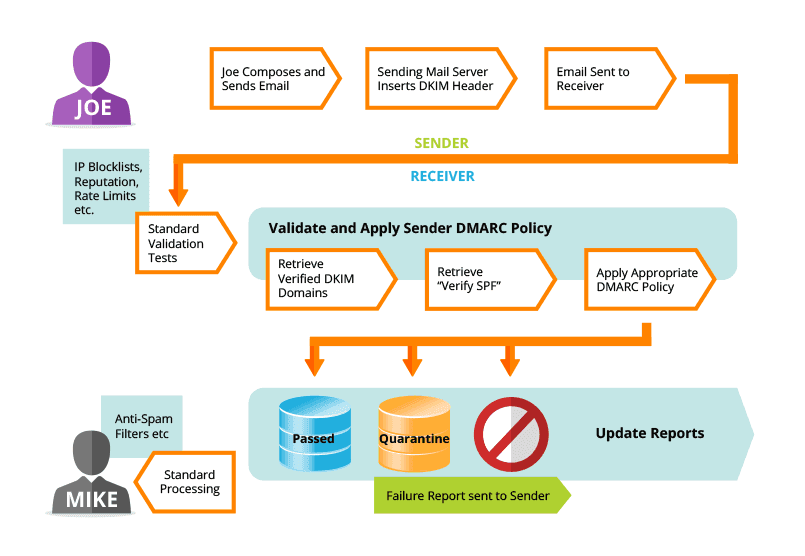
1. Mike’s mailserver receives the connection from the MyCompany Domain. It performs the SPF validation which passes.
2. Mike’s mailserver then retrieves the DMARC policies for the email from the My Company domain and then downloads the full email from the MyCompany mailserver.
3. Mike’s mailserver then does the DKIM check which passes the checksum validation.
4. As both SPF and DKIM have passed, the DMARC policy states that the email can be delivered to the end user (Mike’s mailbox)
5. A report is sent to the email address for the My Company domain (usually set up as a daily report) stating that the emails to Mike’s mailserver where successful.
A phisher tries to send Mike an email, pretending to be from [email protected]
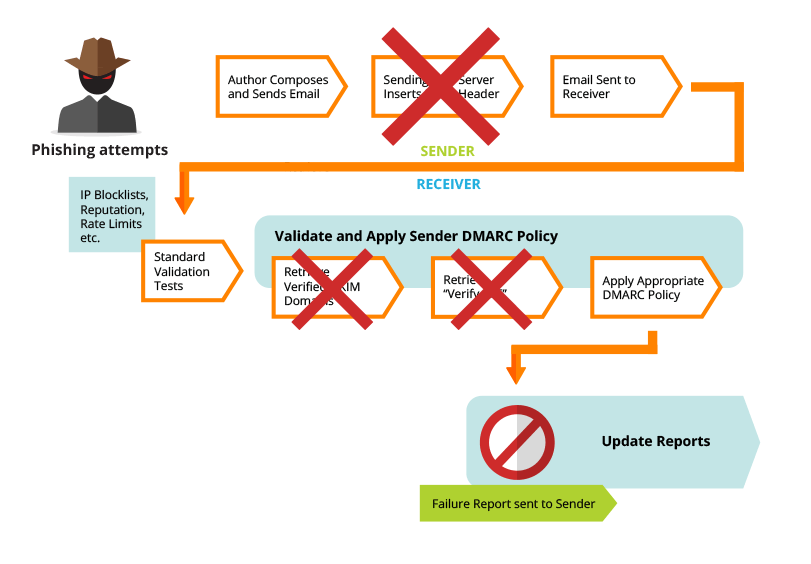
1. Mike’s mailserver receives the connection from the MyCompany Domain. It performs the SPF validation which passes.
2. Mike’s mailserver then retrieves the DMARC policies for the email from the My Company domain and then downloads the full email from the MyCompany mailserver.
3. Mike’s mailserver then does the DKIM check which passes the checksum validation.
4. As both SPF and DKIM have passed, the DMARC policy states that the email can be delivered to the end user (Mike’s mailbox)
5. A report is sent to the email address for the My Company domain (usually set up as a daily report) stating that the emails to Mike’s mailserver where successful.
A phisher tries to send Mike an email, pretending to be from [email protected]
Improve the customer experience with secure document delivery today















