
The large ISPs like AOL, Hotmail, Yahoo! and Gmail are using email sender authentication as an important layer in their spam fighting arsenal. By setting up a system as an authenticated sender, you can instantly bypass certain filters, giving your campaigns a better chance of arriving in your customers’ inbox. Also, many ISPs like Yahoo! and Hotmail will flag your email as authenticated, which helps to build trust between you and your subscribers – ultimately increasing the chance of your emails being opened.
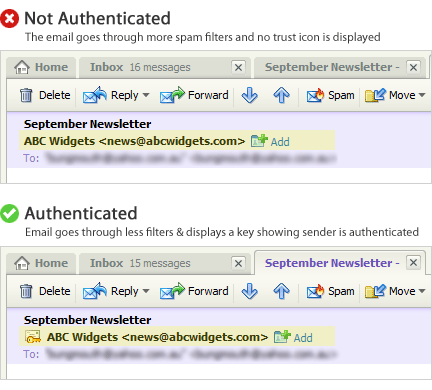
Email sender authentication is all about verifying that the domain used in the ‘from’ address is under the control of the sender.
Sender Authentication jargon and what it all means
ISPs use certain methods to authenticate a sender – SPF & DKIM. Without this additional scrutiny or the correct authentication methods in place your messages could be seen as phishing scams. This makes email authentication an important tool because it impacts directly on email deliverability.
Some terms you need to know that directly impact your deliverability if not set up correctly:
![]() SPF – Sender Policy Framework: This is a way to say an IP or domain can send email on your behalf. It prevents ‘from’ address spoofing.
SPF – Sender Policy Framework: This is a way to say an IP or domain can send email on your behalf. It prevents ‘from’ address spoofing.
![]() DKIM – (DomainKeys Identified Mail): A means to digitally sign an email message and associate a domain name with it. This signature gives recipients and ISPs a reason to believe the email message was created by a known sender and that it was not altered in transit.
DKIM – (DomainKeys Identified Mail): A means to digitally sign an email message and associate a domain name with it. This signature gives recipients and ISPs a reason to believe the email message was created by a known sender and that it was not altered in transit.
![]() DMARC– (Domain-based Message Authentication, Reporting and Conformance): A DMARC policy allows a sender to indicate that their emails are protected by SPF and/or DKIM, and tells a receiver what to do if neither of these authentication methods pass – such as send to junk or reject the message.
DMARC– (Domain-based Message Authentication, Reporting and Conformance): A DMARC policy allows a sender to indicate that their emails are protected by SPF and/or DKIM, and tells a receiver what to do if neither of these authentication methods pass – such as send to junk or reject the message.
All three of the above records are controlled by adding DNS (Domain Name Server) records on your email sending servers.
Why go through all this trouble?
Email authentication is even more crucial when delivering confidential documents. The need for adequate security is a pre-requisite for any eBilling and electronic document delivery project. It is critical that these emails are not only delivered to all recipients, but that only the intended recipients open and view the encrypted email attachment. Customers want confidentiality and assurance that the messages come from a legitimate source.
It’s imperative that these records are set up for your email campaigns. Apply these authentication methods to give you the best running start to getting your emails delivered. There are so many other factors that could affect your deliverability; email authentication shouldn’t be one of them.
Are your emails authenticated? To understand how Striata approaches encryption for secure document delivery, download this free document.

Striata PDF Security Technical Overview
Striata PDF Security Technical Overview - Protecting customer information is a fundamental principle of business. Today, sensible business practice advocates the encryption of any customer information sent over the public internet. Interception of customer information by unauthorized parties has proved an expensive error for many companies. Striata delivers and presents bills, statements and invoices via securely encrypted email attachments. One of he options for this document security is the use of Adobe's Portable Document Format (PDF) encryption. (The encrypted PDF is attached to the email)
Improve the customer experience with secure document delivery today














