
Think of any high volume, system generated paper document that you currently print and deliver by mail and chances are you’re already working towards converting each one to electronic delivery.
But what about security, confidentiality and non-manipulation? How do you ensure trust and compliance with your new process?
Our special blog series is going to look at every aspect of document security and how you can deliver secure eDocuments with confidence.
Opening the envelope vs. opening the email

Let’s start with traditional mail. A piece of paper sitting in your post box is hardly secure, it can be removed read, changed and replaced without your knowledge – it follows that any level of security associated with an electronic document already makes it a better option. However post does have one thing going for it – you have to physically go to each post box to collect mail.
Unlike post boxes, websites (and the now standard customer portal) are publically accessible, so the security requirements immediately become more stringent. Registration and multiple levels of authentication become necessary, but also cause usability and liability issues.
So, you have ease and convenience on one hand vs. barriers and a (good) dollop of effort on the other. What’s the middle ground? Email of course. In a nutshell, an email address is an online version of a post box but with the benefits of cool tech that can be layered on top to make it far more secure than its paper counterpart.
9 Reasons why you should consider sending documents via email
 | Cost take out: Significantly reduces paper, printing and postage costs. Low cost of implementation and pay per use pricing. |
 | Convenience of email and secure attachments: Ability to save the attachment, view it offline and print hard copies. Advanced functionality included within the electronic document. |
 | Security: The eDocument remains encrypted offline and outside the mail client, protecting confidentiality. The email attachment is secured using the latest in encryption technology. |
 | Days Sales Outstanding (DSO): email billing can dramatically reduce a company’s days sales outstanding by cutting the time it takes to get bills to customers and to elicit payment. |
 | Support for corporate e-communication and CRM initiatives: Promotes interaction and direct communication with customers. |
 | Drives qualified web traffic: Augments and complements existing online services. |
 | Marketing: Provides effective marketing real estate that can be used for personalized, targeted marketing offers. |
 | Customer experience insight: Enables detailed tracking reports. |
 | Environmental impact: Minimized by reducing paper output. |
Security and its role in eDocument delivery
I trust you now agree that sending documents to the inbox is a good idea. The next step is to explore all the security aspects of electronic document delivery in detail. Because it’s a big theme we’ll look at each aspect on its own over the next few weeks, including:
- Encryption – which I’ll cover in this blog post
- Password strength: Your document password shouldn’t be the weak link in your secure application chain
- Data protection: Security measures for your eDocument data
- Usability & customer convenience: Ensure your paperless gateway isn’t locked too
Understanding Encryption/cryptography
Banks use 128 bit encryption to protect communications on Internet Banking. We believe electronic document delivery encryption levels from 128 bit and above are sufficient. Let me explain why and how it all works:
Some quick terminology to help you:
- Encryption is a process of scrambling data from its original format into one that is unreadable except by authorized persons, by using one or more algorithms and keys
- The information needed to take data from one format to another is called an “encryption/decryption key”
- The original format is called “plaintext” and the scrambled data is called “ciphertext”
Different encryption schemes
There are two basic types of encryption schemes: Symmetric-key and Asymmetric-key (also called public-key encryption)
Symmetric algorithms – uses the same key to encrypt and decrypt the message
- 3DES – Data Encryption Standard.
- AES – Advanced Encryption Standard
- RC4 – also known as ARC4 is used in protocols such as SSL (to protect Internet traffic), WEP and WPA (to secure wireless networks)
Asymmetric algorithms – uses a different cryptographic key to encrypt and decrypt the message
- PKI – Public-key infrastructure
However, sticking to Symmetric algorithms is advisable because it takes away the requirement for complicated key exchanges. For PKI encryption the consumer has to “have something” (e.g. a private PKI Key) rather than for symmetric encryption where they just have to “know something” (e.g. a type of password).
Key strength
In cryptography, size does matter. The larger the key, the harder it is to crack a block of encrypted data. Typical key strengths are:
- 128bit (RC4)
- 168bit (3DES)
- 256bit (AES)
A password is converted into a key length appropriate to the chosen algorithm.
A brute-force attack consists of systematically checking all possible keys until the correct key is found. The resources required for a brute-force attack grow exponentially with increasing key size. However the key combinations depend on the length of the password that generated the key. Hence the longer the password the harder it is to crack.
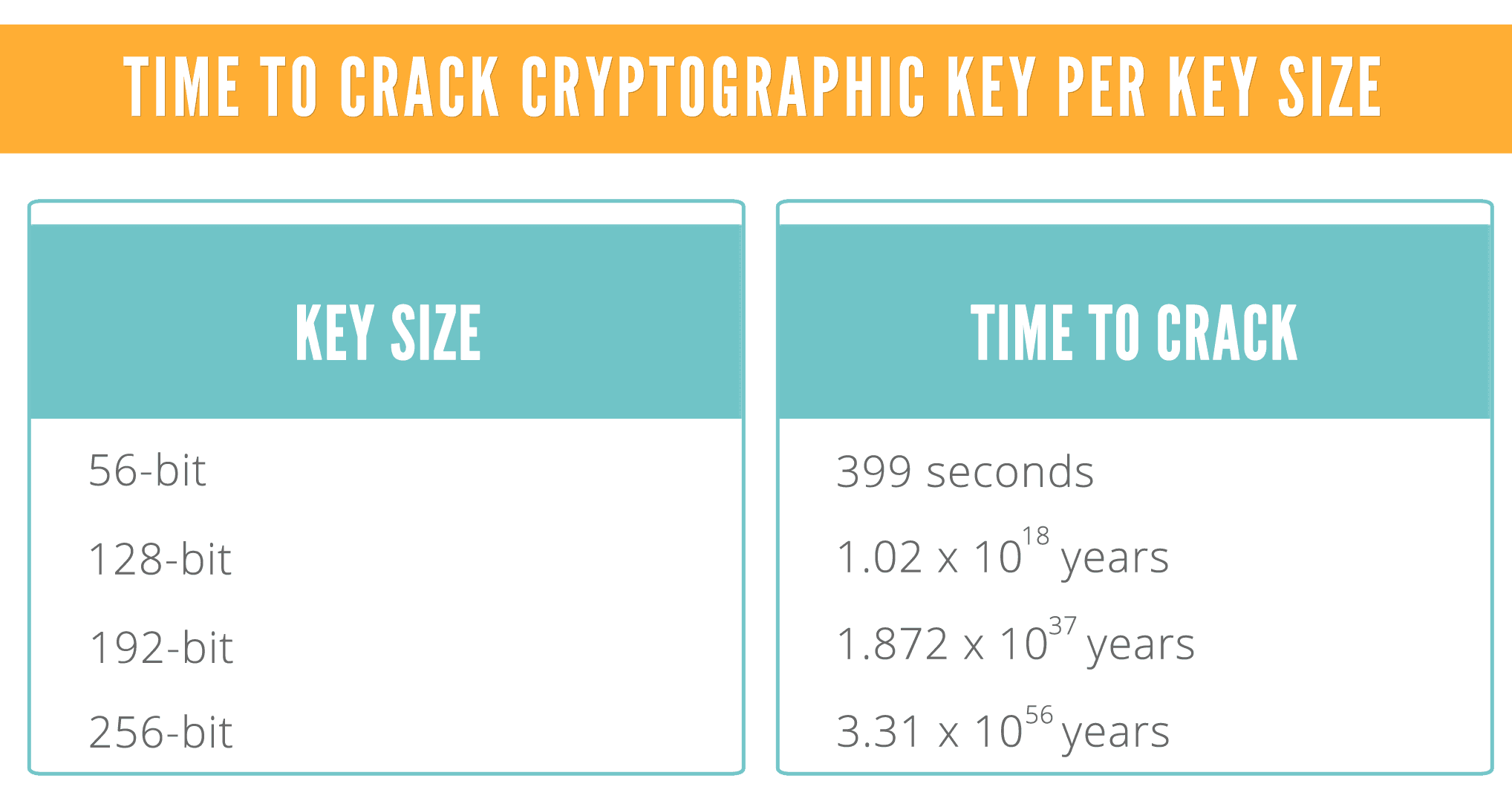
Maybe this is why hackers don’t generally attack the actual encryption; instead they try to “guess” the correct password… in our next post in this email security series we will detail how password strength works in conjunction with encryption.
Keen to get more expert advice on email security? Ge in touch with one of our encryption experts.
Improve the customer experience with secure document delivery today















