
Keeping your customer documents secure
With the increase in frequency and sophistication of cybercrime, involving the theft of personal information – is your organization doing enough to help customers ensure the confidential information you send them remains secure?
Consumer trust is a major challenge in today’s digital age, where cyber-crime escalates in volume and sophistication every year.
This, coupled with the introduction of data privacy legislation such as the EU General Data Protection Regulations (GDPR) and California Consumer Privacy Act (CCPA), has made organizations up their investment in securing personal information while it’s in their care – during processing or stored on their systems.
Once personal information has been sent to the customer in the form of a document, it could be argued that the organization’s responsibility ends there.
But, if your customer’s personal devices are unsecured, there is still a risk that one gets hacked or stolen, which puts all information on that device at risk, including customer documents. Confidential information sent by your organization could find its way into the public eye, or worse, get exploited for the purposes of a crime.
It may not be a breach of your organization’s information security, however, your reputation may still be tarnished, and you may lose the customer, despite the blame being misdirected.
Cybercrime statistics escalate at a frightening rate each year
Cybercrime is a serious threat and every year it rears its ugly head and dominates news headlines worldwide. Unfortunately, technological advancements open new opportunities for more sophisticated cybercrimes.
Not only is technology expanding the boundaries of criminal opportunities, but consumer adoption of various technologies and devices continues to provide a larger market to target.
Read more about What cyber crime will look like in 2020 on TechRadar
Mobile phone theft is a lucrative business
Take the sheer number of mobile phones in the world – which Statista estimates to be 14.9-billion in 2020 and forecasts an increase to 16.8-billion in 2023.
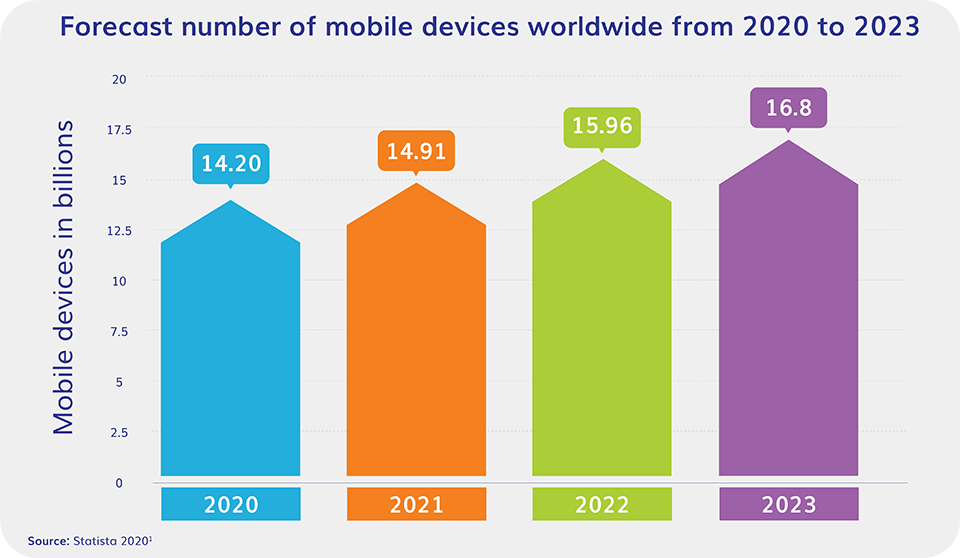
It’s no surprise that the number of mobile phones stolen each year reaches into the millions. It’s not only the phone hardware that criminals want for the resale value, it’s also the data on the device that can be harvested and sold multiple times on the black market.
For the victim, the theft of the device alone is distressing, but even more so, the thought of personal information accessible from that device being used in future crimes, such as identity theft and fraud.
More emails, more phishing, more malware
Aside from the threat of physical device theft, there is also the continually escalating risk of cyberattacks from various directions.
Email remains an important communication channel, especially for business messaging, which unfortunately also makes it a means to target a large audience with a variety of scams.
There’s an estimated 4.4 billion email users worldwide, and 124.5 billion business emails sent per day.
Customers are still falling victim to phishing attacks that expose their personal information.

What is phishing?
Phishing refers to email scams with the purpose of identity theft. Identity thieves send fraudulent email messages with return addresses, links, and branding that appear to come from banks and other legitimate companies. These messages are designed to extract personal and financial information (e.g. passwords, usernames, social security numbers, credit card numbers, etc.) that can then be used for fraud.
Arm yourself with information on the Top Phishing Trends to Keep an Eye On in 2020
Another way to attack customers by email is to trick them into opening an attachment or clicking on a link that contains malware.

What is malware?
Malware is a broad term that refers to a variety of malicious programs, the most common types being spyware, Trojan horses, viruses, and worms. These programs use various hooks to trick a victim into opening an attachment or URL, which then allows the malware to install itself on the host machine. Once that occurs, the program proceeds to harvest data, infiltrate the network or delete files and directories.
According to Kaspersky Labs, the number of unique malicious objects detected by its web antivirus solution reached 24,610,126 in 2019. 85% Of web threats detected were malicious URLs – making the risk of a customer unwittingly clicking on a URL an ever present threat to data protection.

COVID-19 fears create a rich hunting ground for cybercriminals
Cybercriminals are quick to take advantage of world events as a fresh approach to finding victims. Using the awareness and fear generated by the global spread of the novel coronavirus (COVID-19) as a hook, phishers are ramping up campaigns that purport to be from legitimate sources like the World Health Organization.
Criminals are clever – the content is highly relevant and the tone adds a sense of urgency and stress. But, if the recipient clicks on the link or attachment, they are taken to a spoofed web page which will steal their personal information or infect their device with malware.
Read more about how to protect yourself in Time’s article: COVID-19 Scams Are Everywhere Right Now. Here’s How to Protect Yourself.
In short, while organizations are increasingly aware of the need to protect their customers’ personal information under their care, there are constant threats to that same information when it resides on the customer’s personal devices.
Data protection obligations cover the entire information lifecycle
The golden standard in data privacy legislation – the EU GDPR – is clear on an organization’s obligations to protect data in its care. This extends to doing everything it can to protect information throughout its lifecycle.
Through the concept of ‘data protection by design and by default’, the regulations state that organizations must integrate or ‘bake in’ data protection into processing activities and business practices, from the design stage, right through the lifecycle.”
According to the ICO, data protection by design is about considering data protection and privacy issues upfront in everything you do. It can help ensure that you comply with the GDPR’s fundamental principles and requirements, and forms part of the focus on accountability.
It goes without saying that an organization processing personal information must have appropriate safeguards to protect sensitive data. But, many have not considered that these safeguards must extend beyond the reach of the organization, to the individual’s device.
Organizations must do everything in their power to ensure the safety of their customers’ confidential documents
Aside from the legal obligation, there’s also a logical, self-preservation element to protecting data throughout the lifecycle.
While bad news travels fast when a customer’s personal data is exploited, the fact that it was breached outside of the organization that provided it, doesn’t always filter through. This can lead to undeserved reputational damage.
It makes sense for organizations to do everything in their power to ensure that the personal information they generate remains secure. Not only while processing or storing the information, but even when it resides on the customer’s device.

Helping customers be safe
Organizations need to ensure that the information they provide to customers, continues to be protected throughout its lifecycle. This includes documents that the customer is emailed or able to download.
Encrypting and protecting important documents ensures that even when it resides on the customer’s smartphone or laptop, the information cannot be easily accessed if the device is stolen or hacked.

Encryption
A process that encodes a message or file so that it can only be read by the intended recipient. Encryption scrambles, or encrypts data which only the receiving party can unscramble, or decrypt, using a key (a string of values or an application).

Password protection
Means a document cannot be opened without entering a shared secret known only to the sender and recipient. Requiring a password to access a secured document not only adds another layer of protection, but has other benefits.
In the unlikely event that a document is sent to the wrong person, the incorrect recipient cannot open the document (personal information remains private), thereby avoiding a data breach.
Regardless of the format in which information is shared – be it HTML, PDF, XML – the file needs to be encrypted and preferably password protected, to ensure the privacy of the confidential information it contains.
Customer education is key to data protection
Educating your customers is the most powerful way to avoid risky behavior and help them protect their personal information.
While it’s important the organization does everything possible to secure personal data through the entire lifecycle, the reality is that cyber-criminals keep getting smarter, which means new and more sophisticated ways of tricking your customers.

How to ensure your customers don’t fall victim to phishing scams:
- Constantly inform your customers about what they can expect to receive from your organization by email.
- Be clear about what you will never request by email – such as a pin number, security login or credit card details.
- Teach them to be suspicious of any email they are not expecting, especially if it includes a request or instruction to open an attachment, click on a link or provide personal information. It’s a good idea to use examples and scenarios to illustrate risky behaviors.
- Notify them of your official sender domains and explain how to check the sender domain of a suspicious email. Unfortunately, it is getting harder to recognize a scam simply from the sender address, as phishers are getting more sophisticated in their domain choices.
- Ask your customers to report any emails where your brand is being impersonated. Have a clear process for anyone to report a scam to your security team for further investigation.
How to improve security of a mobile phone
Mobile phones are computers too. They are often overlooked as a device that needs protection, yet they are used extensively to interact with your company’s communications, apps, and portals.
Advise your customers to:
- Set a screen password and have it auto-lock after 3 minutes
- Install an antivirus application
- Encrypt the mobile device, so that the phone’s data is unreadable if stolen
- Use two-factor authentication on all apps and portals that offer this security option
- Don’t access public Wifi and avoid charging in public ports
Customer education is not a once-off exercise, it requires consistent and regular communication to help identify security threats, reinforce the right behavior and minimize risk.

How Striata can help
As a digital communication specialist, our reputation is built on our ability to keep the information entrusted to us, safe and secure. We know that information security is not a destination – it is a journey we take alongside our clients, to constantly mitigate the many risks of an ever-changing cyber-landscape.
Striata’s secure document solutions ensure that personal information inside confidential documents is protected throughout the lifecycle. Our clients can be assured that their customer data is subject to the highest level of security, from the source system right through to the customer’s desktop or mobile device.
Secure Document Solutions
- Secure Document Delivery (SDD) enables the generation and distribution of high volumes of documents by email. Confidential documents sent through our platform are encrypted and password protected to ensure the protection of personal data, even when on the end-user’s device.
- Secure Document Repository (SDR) is a fast, secure and easy to integrate platform for accessing electronic documents online. Designed to plug into an organization’s existing customer portal, the SDR provides a secure and robust interface for electronic presentation of many types of documents. Customers can access, search for and retrieve their electronic documents themselves, rather than following other slower, more expensive channels.
- Secure Document Presentation (SDP) solution is a highly secure method of providing online access to information contained in confidential documents. Documents are available online (as an interactive web or PDF experience) to be viewed via a browser or applicable application.
Our platform is built with the security of data and processes as a core priority. We ensure that data passing through our platform is protected by multiple layers of security, including when in transit, during processing and when on the user’s device.
- Our platform and processes have passed numerous third-party audits, by both professional assessors and client security teams. Audits are done annually to check vulnerability, based on new industry attack vectors.
- Our information security management processes are ISO 27001 certified.
- Production platforms are cloud-based and hosted with providers that meet industry standards for security and compliance. Cloud providers are evaluated on an annual basis, which includes reviews of their independent security and procedures audits.
- To secure information on the end-users’ devices, our platform uses 256bit encryption to protect confidential documents that are sent from our platform.
We have also built flexibility into our platform and our processes. The platform supports multiple input formats, several secure transfer protocols and a range of output formats – such as PDF documents, encrypted HTML pages.
Ensure that the information you provide inside confidential documents, continues to be protected, even when residing on the customer’s personal device.



